What Is 3D Printing?
3D printing, also known as additive manufacturing, refers to a process of creating three-dimensional solid objects from a digital file. The creation of a 3D printed object is achieved using

Building the Cyber Defense Line: Your Incident Response Team is a crucial exploration into the heart of cybersecurity—a field that has never been more essential as our world grows increasingly digital and interconnected. This topic delves deep into the specialized roles and diverse skill sets required to effectively respond to and mitigate the impact of cyber threats, safeguarding the digital assets and operations of organizations across the globe.
In the vast expanse of the internet, where data flows like the lifeblood of modern civilization, the importance of a robust cybersecurity defense cannot be overstated. Cyber attacks are not just frequent; they are evolving, becoming more sophisticated, and their potential to disrupt business operations and compromise sensitive information is escalating. Against this backdrop, the role of incident responders emerges as the cornerstone of a proactive cybersecurity strategy. These are the professionals who stand on the front lines, equipped with the knowledge and tools to fend off attackers and protect the digital domain.
The introduction to “Building the Cyber Defense Line” will shed light on the multifaceted nature of the cybersecurity incident response (IR) specialization. It begins with a fundamental understanding of what incident response entails: a set of procedures and actions taken to promptly identify, investigate, and remediate cyber threats. Incident response is not merely about reacting to attacks; it’s about preparing for them, understanding them, and building a resilient infrastructure that can withstand the inevitable breaches and minimize their impact.
This exploration will guide readers through the critical roles within an incident response team—from the Incident Manager, who oversees and coordinates the response efforts, to the Technical Lead, the Communications Manager, the Digital Forensics Analyst, and more. Each role is a vital piece of the puzzle, contributing unique skills and perspectives to manage and mitigate cyber incidents effectively.
Moreover, the topic emphasizes the essential skills and competencies necessary for success in incident response. These range from technical proficiencies like network traffic analysis, malware analysis, and digital forensics, to soft skills such as critical thinking, effective communication, and problem-solving. In the dynamic and high-pressure environment of incident response, these skills are indispensable tools in the responder’s arsenal.
“Building the Cyber Defense Line” aims to illuminate the path for those aspiring to enter the field, while also providing valuable insights for organizations looking to strengthen their cybersecurity posture. As cyber threats continue to evolve, so too must our defenses. This introduction sets the stage for a deeper understanding of the key roles and skills in incident response, underscoring its significance in the ongoing battle to protect our digital world.
Our robust CompTIA Sec+ course is the perfect resouce to ensure your company’s most valuable assets are safe. Up your security skills with this comprehensive course at an exceptional price.
Discuss the pivotal role played by incident responders in maintaining the security and integrity of an organization’s information systems. Outline their responsibilities, which include monitoring systems for signs of intrusion, assessing the severity of threats, conducting forensic analysis to trace the source of breaches, and implementing strategies to prevent future incidents. Mention how their work supports the organization’s broader cybersecurity framework and aids in compliance with regulatory requirements.
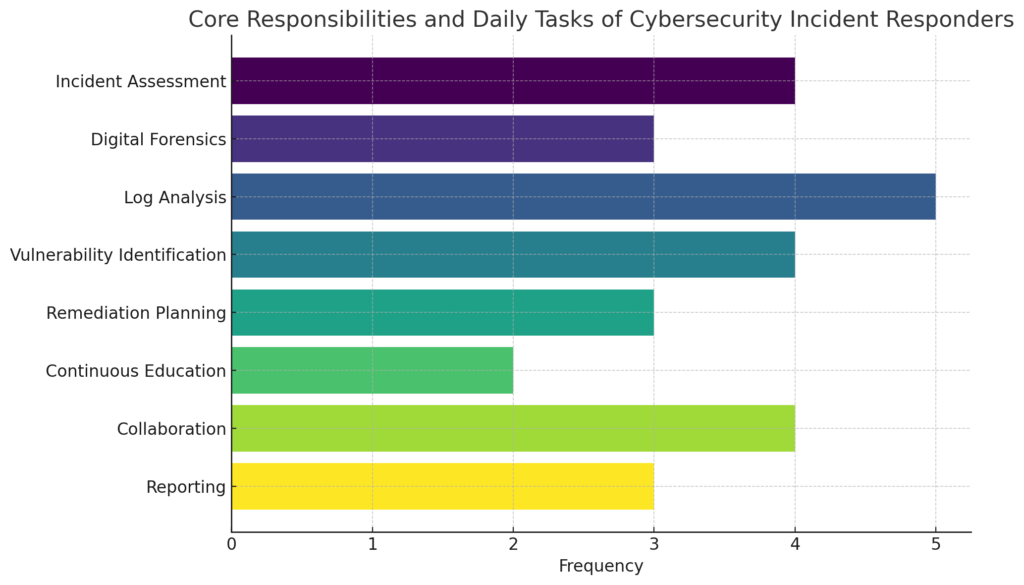
The chart above visualizes the core responsibilities and daily tasks of cybersecurity incident responders, highlighting the frequency with which each task is typically performed. Tasks such as “Log Analysis” are shown to occur with the greatest frequency, underscoring the importance of continuous monitoring and analysis in identifying potential security threats. Other tasks like “Continuous Education” are less frequent but equally critical, emphasizing the need for incident responders to stay updated with the latest cybersecurity trends and techniques. This chart serves as a snapshot of the varied and dynamic role that incident responders play in safeguarding an organization’s digital assets.
Building an effective Incident Response (IR) team is pivotal in preparing for and addressing cybersecurity incidents that could potentially disrupt operations, compromise data, and harm an organization’s reputation. An IR team is a specialized group of professionals with diverse skills and roles, each contributing uniquely to the detection, analysis, response, and recovery from cybersecurity threats. Here’s a deeper look into the essential roles within an IR team and how they collectively fortify an organization’s cyber defense:
The Incident Manager acts as the orchestrator of the incident response process. They are responsible for initiating the IR plan upon detection of a security incident, coordinating the response efforts across the team, and ensuring that actions are taken swiftly and effectively. The Incident Manager prioritizes tasks, allocates resources, and keeps the response on track, all while maintaining an overview of the incident’s scope and impact. Their leadership ensures that the team operates as a cohesive unit and that the incident is resolved in a manner that minimizes damage to the organization.
Technical Leads or SMEs possess deep technical knowledge in specific areas, such as network security, malware analysis, or digital forensics. They analyze the technical aspects of the incident, identify the attack vectors, and determine the extent of the compromise. By dissecting the nature of the threat, Technical Leads provide critical insights that guide the response strategy, ensuring that remediation efforts are both targeted and effective. Their expertise is instrumental in uncovering the root cause of the incident and in preventing similar breaches in the future.
The Communications Manager is responsible for managing all internal and external communications related to the incident. This includes crafting clear, concise, and accurate messages to stakeholders, employees, and potentially the public, explaining the nature of the incident, its impacts, and the steps being taken to resolve it. Effective communication helps to manage expectations, maintain trust, and minimize panic or confusion. The Communications Manager also plays a crucial role in regulatory compliance, ensuring that any mandatory disclosures are made within required timeframes.
The Legal Liaison advises on the legal implications of the incident and the response actions. They ensure that the organization’s response is in compliance with applicable laws, regulations, and contractual obligations related to cybersecurity and data protection. The Legal Liaison works closely with external legal counsel, law enforcement, and regulatory bodies as needed. They also guide the preservation of evidence for potential legal actions and advise on disclosure and reporting obligations, helping to navigate the complex legal landscape that surrounds cybersecurity incidents.
Beyond these core roles, a comprehensive IR team may include other specialists depending on the size and nature of the organization:
An effective IR team is not static; it evolves in response to changing cyber threat landscapes and organizational needs. Each role within the team contributes to a holistic approach to incident response, ensuring that the organization can not only respond to and recover from cyber-attacks but also strengthen its defenses against future threats. Collaboration, continuous learning, and adaptability are key traits that underpin the success of any IR team, enabling them to protect the organization’s digital assets and reputation in an ever-changing cyber environment.
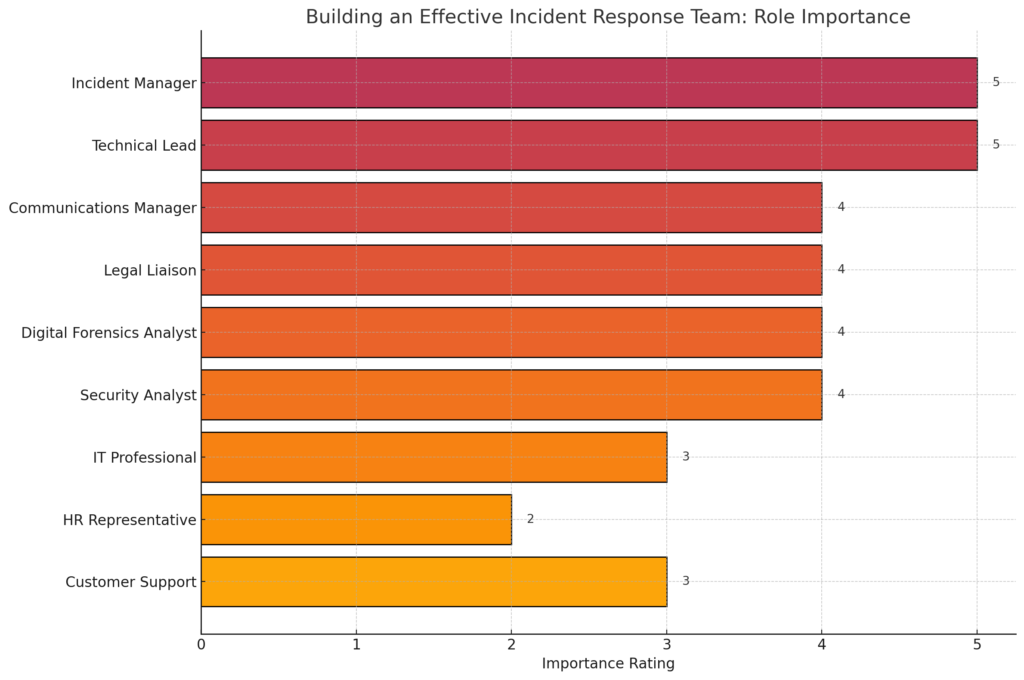
The chart above visualizes the importance of various roles within an effective incident response team, based on a hypothetical importance rating scale from 1 to 5. This illustrates not only the diversity of skills and areas of expertise required to manage and mitigate cybersecurity incidents but also highlights the critical nature of roles such as the Incident Manager and Technical Lead, which are fundamental to orchestrating the response effort. Other roles, while rated slightly lower in this illustrative scale, are nonetheless essential to ensuring a comprehensive approach to incident response, encompassing legal compliance, communication, forensic analysis, and support functions. This chart underscores the collaborative effort required to build a resilient and responsive cybersecurity posture.

Propel your career forward and be part of an essential member of any management team as an Information Security Manager. This advanced training series is designed specifically for those want to move up into a management position in the IT field.
In the digital age, where cybersecurity threats loom large and the potential for damage is ever-present, the formation and maintenance of an effective incident response (IR) team stand as a critical defense mechanism for organizations worldwide. The journey through understanding the core responsibilities, daily tasks, and the multifaceted roles within an IR team underscores the complexity and importance of a well-coordinated response to cyber incidents.
Building an effective IR team is not a one-time task but a continuous process of adapting to new threats, technologies, and best practices. The Incident Manager, Technical Lead, Communications Manager, and Legal Liaison, among others, form the backbone of a team equipped to tackle the challenges posed by cyber threats head-on. Each role, with its unique set of responsibilities and required skills, contributes to a holistic approach to incident response, ensuring that an organization can not only withstand and recover from attacks but also emerge stronger and more secure.
The importance of each role within an IR team, as visualized in the chart, highlights the necessity for a diverse set of skills and expertise. From the strategic oversight of the Incident Manager to the technical acumen of the Technical Lead, the clear and concise communication managed by the Communications Manager, and the legal guidance provided by the Legal Liaison, each member plays a pivotal part in the cybersecurity defense line.
As cybersecurity threats continue to evolve, so too must the strategies and compositions of IR teams. The integration of digital forensics analysts, security analysts, IT professionals, and support roles such as HR representatives and customer support, further enriches the team’s capabilities. This comprehensive approach ensures that all aspects of an incident are addressed, from technical analysis and recovery to legal compliance and stakeholder communication.
In conclusion, the creation and continuous improvement of an incident response team are vital to an organization’s cybersecurity posture. The detailed exploration of the roles and skills necessary for an effective IR team highlights the complexity of responding to cyber incidents and the importance of preparedness and resilience. As organizations navigate the challenging landscape of cyber threats, investing in a capable and versatile IR team is not just a strategic choice but a necessity for safeguarding digital assets, maintaining trust, and ensuring business continuity in the face of adversity.
Understanding key terms related to Incident Response Teams is crucial for professionals in cybersecurity. These terms encompass the roles, processes, and tools involved in identifying, assessing, responding to, and recovering from cybersecurity incidents. A well-prepared team can significantly mitigate the impact of cyber threats on an organization.
| Term | Definition |
|---|---|
| Incident Response (IR) | A set of procedures for handling and responding to a cybersecurity incident with the aim of limiting damage and reducing recovery time and costs. |
| Incident Manager | The person responsible for managing and coordinating the incident response process during a cybersecurity event. |
| Technical Lead | A subject matter expert with deep technical knowledge in specific areas such as network security, malware analysis, or digital forensics. |
| Communications Manager | Handles internal and external communications related to the incident, ensuring clear, concise, and accurate messaging to stakeholders. |
| Legal Liaison | Advises on the legal implications of the incident and ensures compliance with relevant laws and regulations. |
| Digital Forensics Analyst | Investigates breaches to gather evidence, understand the attack methodology, and aid in recovery efforts. |
| Security Analyst | Monitors and analyzes security alerts, implements security measures, and assists in the detection and prevention of cyber threats. |
| IT Professionals | Technical staff responsible for maintaining and restoring IT systems and services affected by a cybersecurity incident. |
| Human Resources (HR) | May be involved in cases where insider threats are suspected or in managing personal information breaches. |
| Customer Support Representatives | Address customer inquiries and concerns related to cybersecurity incidents. |
| Network Traffic Analysis | The process of capturing, inspecting, and analyzing network traffic to identify unauthorized activities or anomalies. |
| Malware Analysis | The practice of examining malicious software to understand its functionality, origin, and potential impact. |
| Digital Forensics | The process of uncovering and interpreting electronic data, with the goal of preserving evidence in its most original form. |
| Ethical Hacking | The practice of penetrating networks and systems with the aim of finding and fixing security vulnerabilities. |
| Incident Response Plan (IRP) | A documented plan that outlines the procedures an organization follows when responding to a cybersecurity incident. |
| Threat Intelligence | Information used to understand the threats that an organization faces, including tactics, techniques, and procedures of attackers. |
| Containment Strategies | Measures taken to isolate and limit the impact of a cybersecurity incident. |
| Eradication | The process of removing the cause of a cybersecurity incident and any related malware or vulnerabilities from an organization’s environment. |
| Recovery | Actions taken to restore and return affected systems and devices to their normal, secure state. |
| Post-Incident Analysis | The evaluation of an incident’s handling, aiming to improve future incident response efforts and overall security posture. |
This list provides a foundation for understanding the multidisciplinary approach required in incident response and emphasizes the importance of a cohesive strategy in cybersecurity defense.
The primary role of a Cybersecurity Incident Response Team (IR Team) is to prepare for, detect, analyze, contain, and recover from cybersecurity incidents. The team aims to minimize the impact of any security breach by quickly identifying threats, mitigating damages, and implementing measures to prevent future incidents. This involves a coordinated effort across various specialized roles to ensure an organization’s resilience against cyber threats.
A comprehensive Cybersecurity Incident Response Team should include an Incident Manager, Technical Lead, Communications Manager, and Legal Liaison. Additionally, roles such as Digital Forensics Analysts, Security Analysts, IT Professionals, Human Resources Representatives, and Customer Support should be considered to cover all aspects of incident response, from technical analysis to legal compliance and stakeholder communication.
Cybersecurity Incident Response Teams use a combination of advanced monitoring tools, threat intelligence, and cybersecurity frameworks to identify potential threats. Upon detecting a threat, the team follows a predefined incident response plan that includes steps for assessment, containment, eradication, and recovery. This plan is regularly updated to adapt to new cyber threats and ensure effective response strategies.
Members of a Cybersecurity Incident Response Team need a blend of technical and soft skills. Essential technical skills include network traffic analysis, malware analysis, digital forensics, and ethical hacking. Equally important are soft skills such as critical thinking, effective communication, and problem-solving. Continuous education in the latest cybersecurity trends and threats is also crucial for all team members.
To ensure preparedness and effectiveness, a Cybersecurity Incident Response Team should conduct training and simulation exercises regularly. Ideally, these exercises should be held at least quarterly, but more frequent sessions might be necessary depending on the organization’s size, complexity, and the evolving nature of cyber threats. Regular training helps identify gaps in the incident response plan and improves the team’s response time and coordination.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
$49.99 Original price was: $49.99.$16.99Current price is: $16.99. / month with a 10-day free trial
3D printing, also known as additive manufacturing, refers to a process of creating three-dimensional solid objects from a digital file. The creation of a 3D printed object is achieved using
Access Management refers to the processes and technologies designed to control and manage access to information and systems within an organization. It plays a critical role in ensuring that the
An Ad Hoc Network is a decentralized wireless networking paradigm that allows individual devices to communicate directly with each other without relying on a pre-existing infrastructure, such as routers or
Adaptive User Interfaces (AUIs) are intelligent systems designed to improve user interaction with software applications by automatically adjusting their layout and elements based on the user’s needs, preferences, and context.
Adobe Photoshop is a powerful digital imaging and graphics editing software developed by Adobe Inc. It’s widely recognized as the industry standard for raster graphics editing, used by professionals in
Agile Business Analysis (ABA) is a methodological approach that focuses on delivering business value by integrating business analysis processes with agile principles. It emphasizes flexibility, continuous improvement, and close collaboration
Agile Project Portfolio Management (PPM) is an approach that aligns project, program, and portfolio management practices with agile methodologies. It focuses on flexibility, continuous improvement, and the ability to adapt
Agile Test Automation refers to the practice of automating the testing process in an agile software development environment. It aims to enhance the efficiency and effectiveness of testing by automating
AI Governance is a framework or system designed to ensure the responsible development, deployment, and use of artificial intelligence (AI) technologies. It encompasses a broad set of policies, principles, and
Algorithmic bias refers to systematic and repeatable errors in a computer system that create unfair outcomes, such as privileging one arbitrary group of users over others. This bias can originate
Amazon Web Services (AWS) is a comprehensive, evolving cloud computing platform provided by Amazon that includes a mixture of infrastructure as a service (IaaS), platform as a service (PaaS), and
Continuous Data Protection (CDP), also known as real-time data protection, refers to the method of backing up data by automatically saving a copy of every change made to that data,
ENDING THIS WEEKEND: Train for LIFE at our lowest price. Buy once and never have to pay for IT Training Again.

Get ready for the updated 220-1201 & 220-1202 exams with our brand-new CompTIA A+ training—designed to help you pass with confidence and start your IT career strong. Access this course and over 2,900 hours of expert-led IT training when you sign up for any of our All-Access Passes. Don’t miss out—enroll now and start learning today!